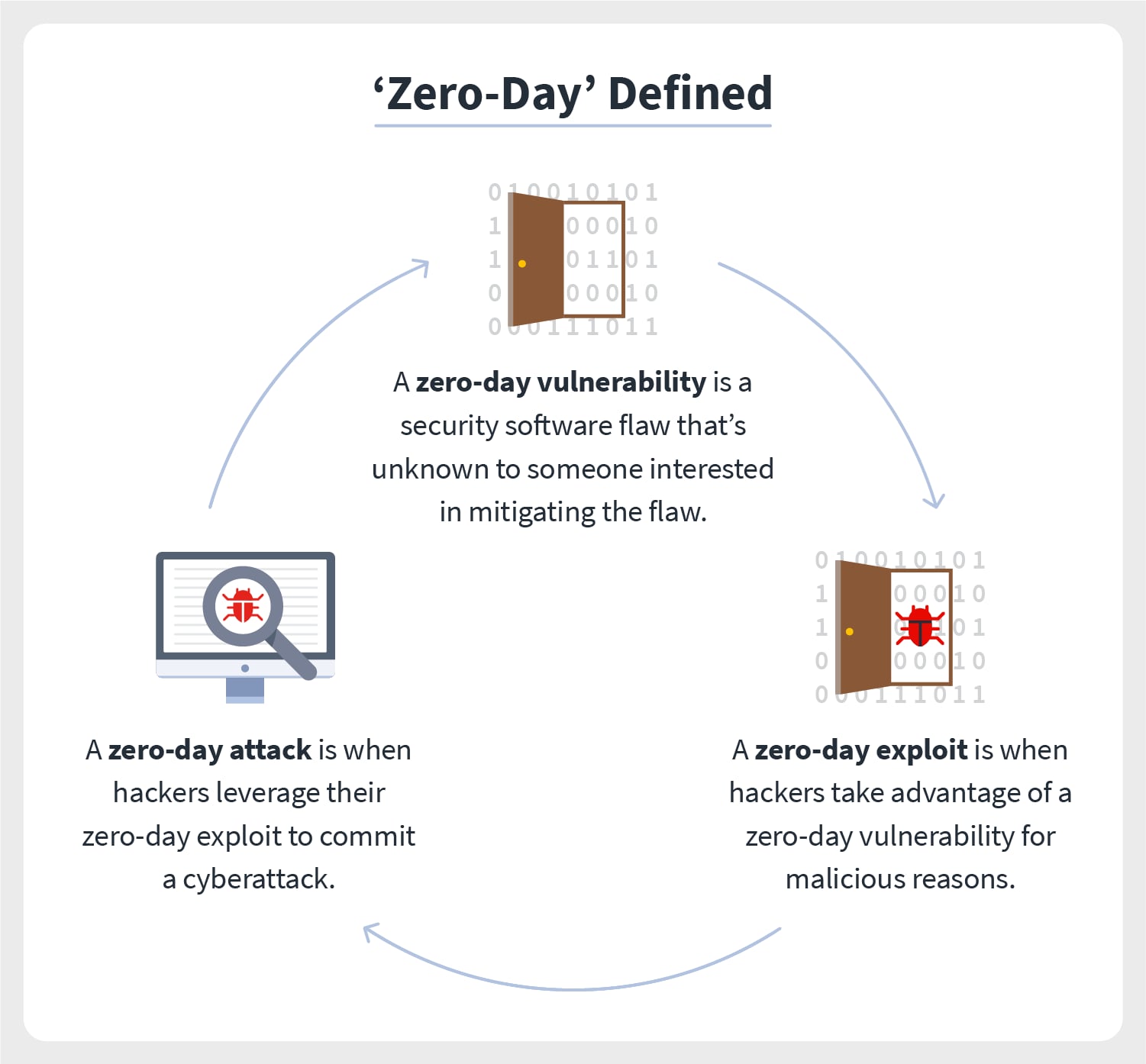
Computer Security, Zero-day Exploit. Computing Vulnerability. 3D Illustration. Perspective and Depth. Stock Illustration - Illustration of depth, design: 200735640
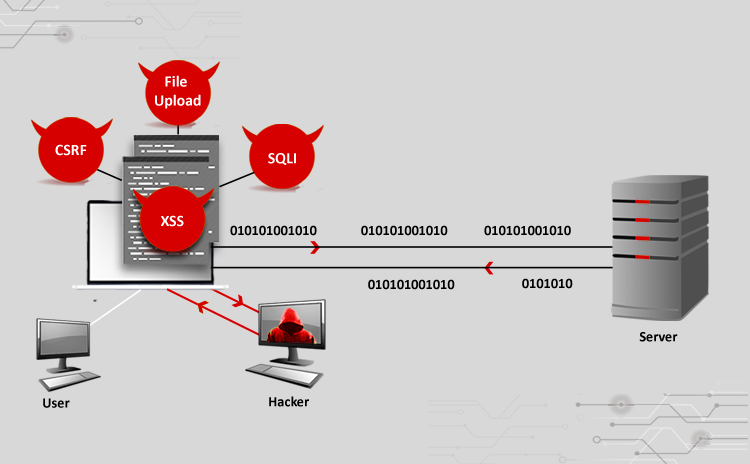
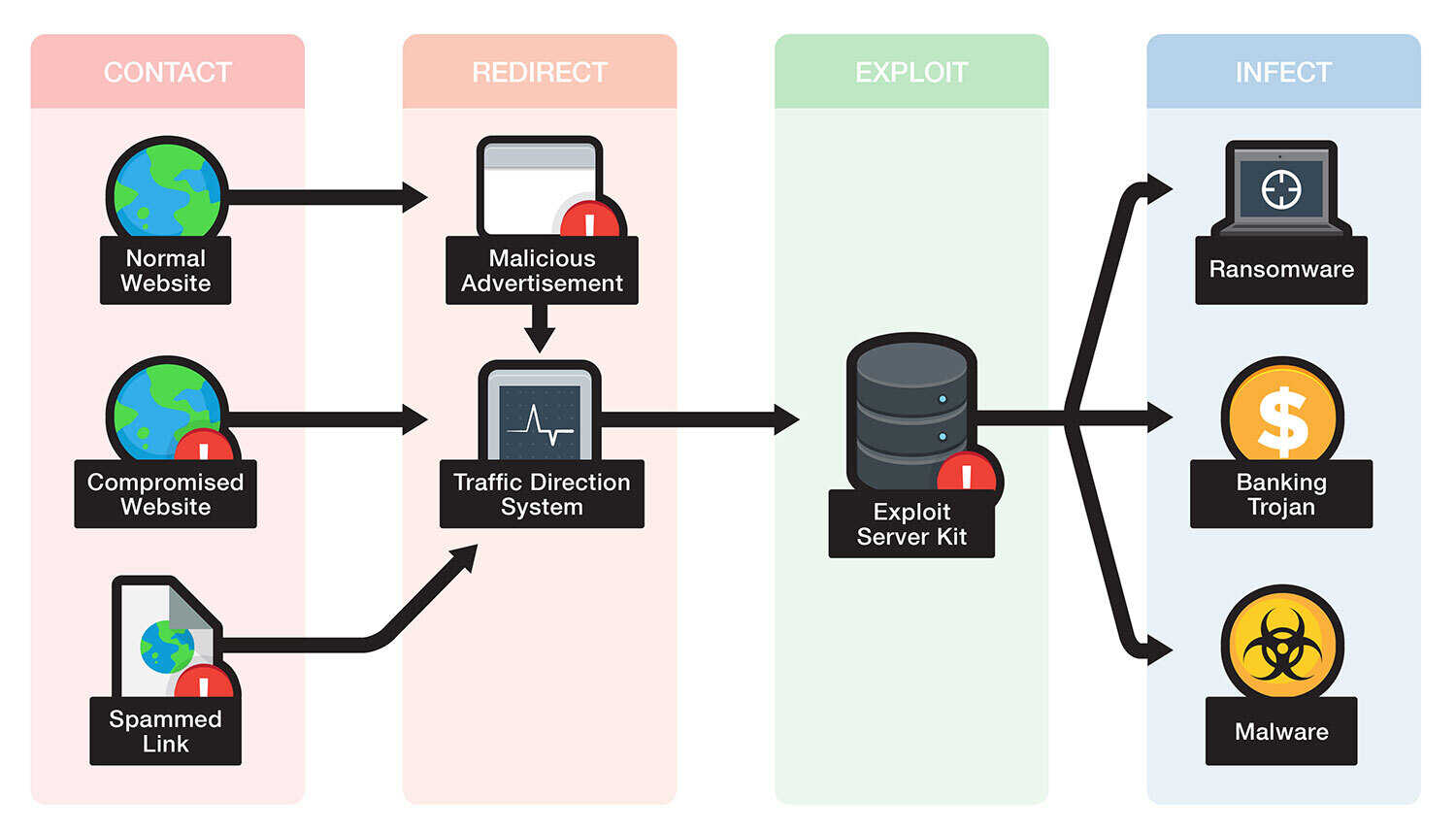
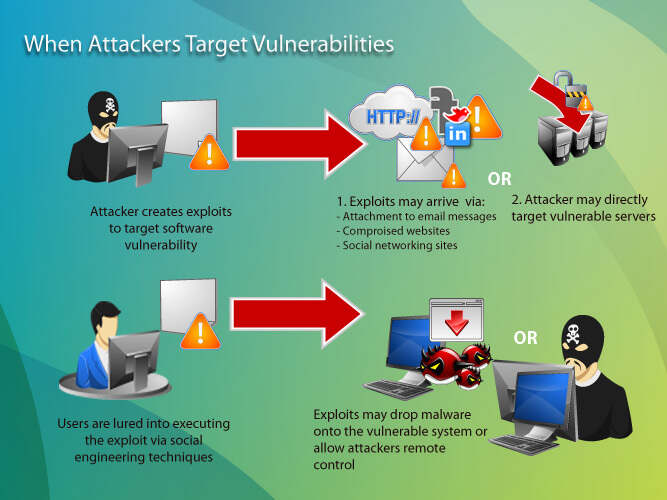
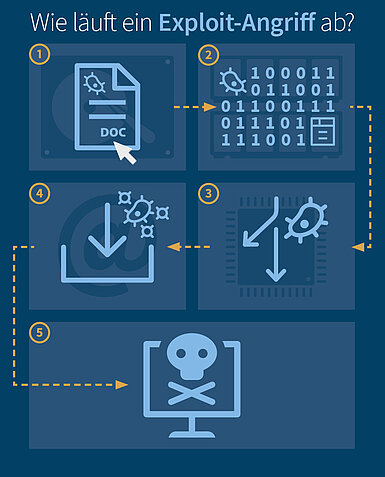
Cyber Attacks Explained - Web Exploitation - Cyber Security Blogs - Valency Networks - Best VAPT Penetration Testing Cyber Security Company - Pune Mumbai Hyderabad Delhi Bangalore Ahmedabad Kolkata India Dubai Bahrain