NSA announces winner of 8th Annual Best Scientific Cybersecurity Research Paper Competition | 2020-12-01 | Security Magazine

PDF) Measuring Cyber Security Awareness of Students: A Case Study at Fahad Bin Sultan University | IJCSMC Journal - Academia.edu

Cyber Security Challenges within the Connected Home Ecosystem Futures – topic of research paper in Computer and information sciences. Download scholarly article PDF and read for free on CyberLeninka open science hub.

Review of Cybersecurity Research Topics, Taxonomy and Challenges: Interdisciplinary Perspective | Semantic Scholar

Static Versus Dynamic Data Information Fusion Analysis Using DDDAS for Cyber Security Trust – topic of research paper in Computer and information sciences. Download scholarly article PDF and read for free on
Computer Security Threats: Small Business Professionals' Confidence in Their Knowledge of Common Computer Threats Thomas Hayes
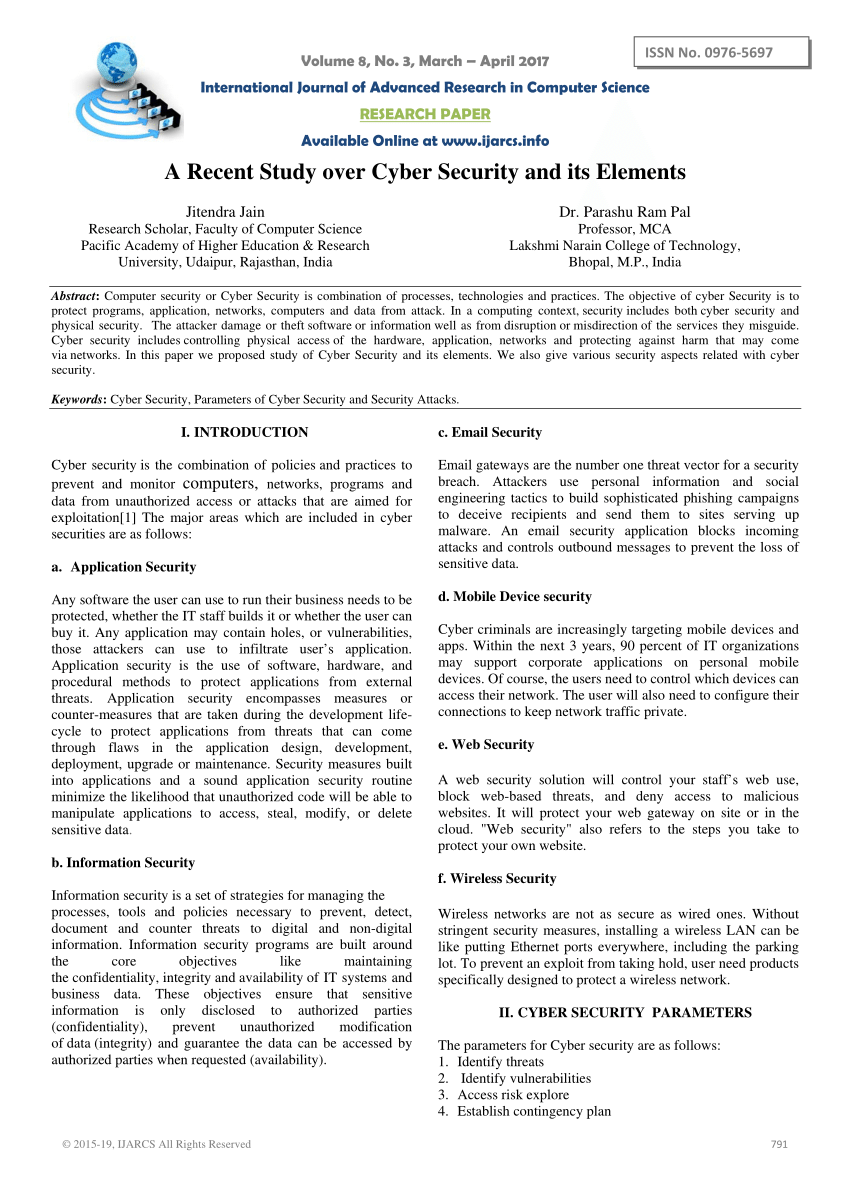
Proposal Example 1 Information and Communications Technology (ICT) has taken a central role in modern society. Unfortunately, ma

Axiomatic Design/Design Patterns Mashup: Part 2 (Cyber Security) – topic of research paper in Computer and information sciences. Download scholarly article PDF and read for free on CyberLeninka open science hub.

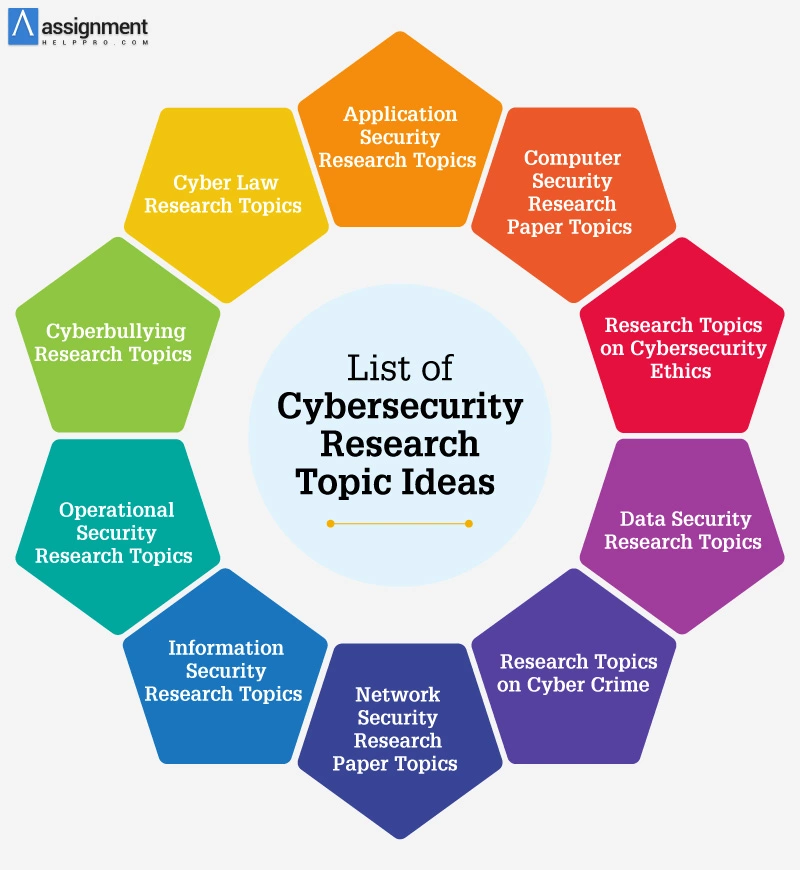
![A List of 181 Hot Cybersecurity Topics for Research Papers [2022] A List of 181 Hot Cybersecurity Topics for Research Papers [2022]](https://custom-writing.org/blog/wp-content/uploads/2021/04/steps_5_arrow_cyber-1024x449.jpg)