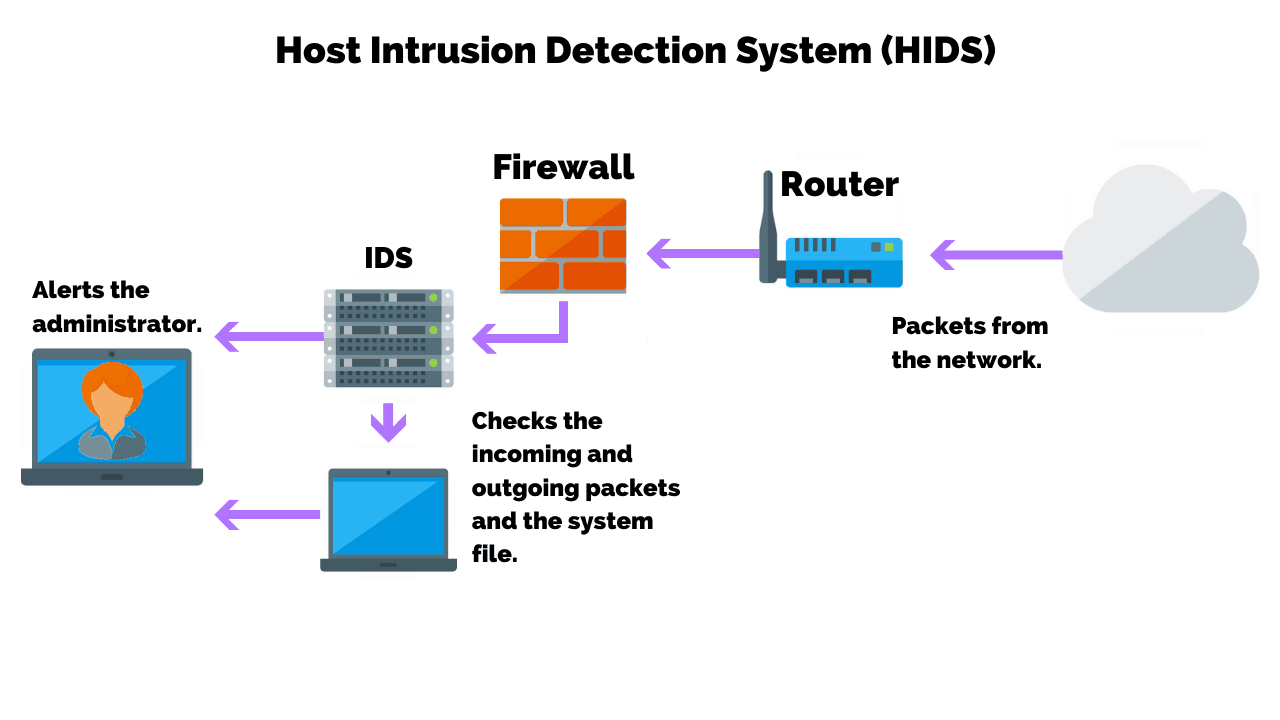
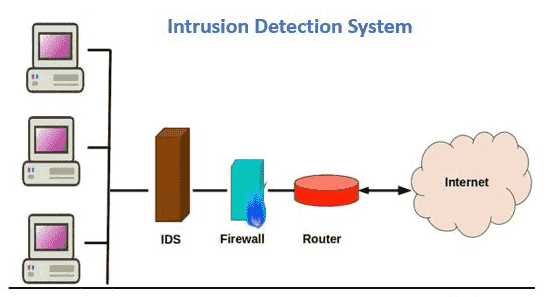
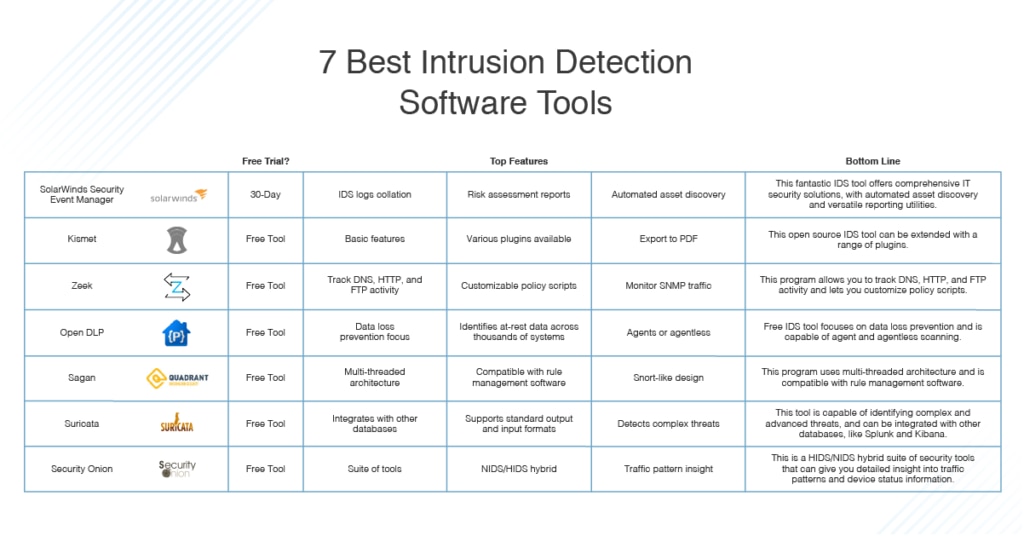
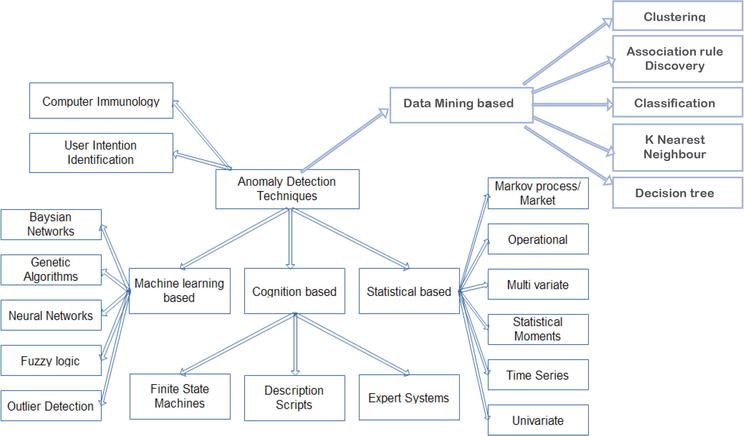
Network intrusion detection system: A systematic study of machine learning and deep learning approaches - Ahmad - 2021 - Transactions on Emerging Telecommunications Technologies - Wiley Online Library
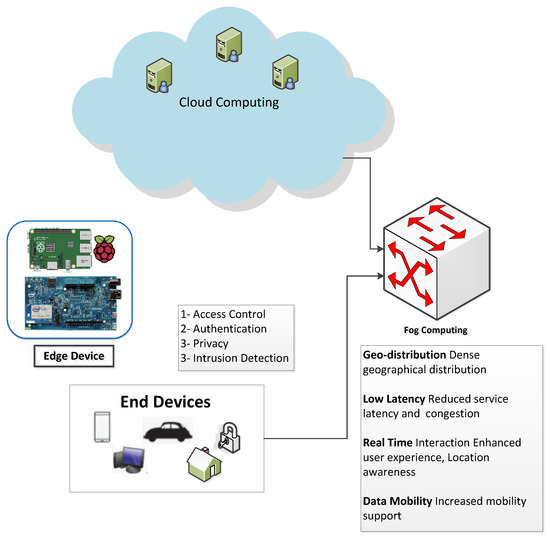
Applied Sciences | Free Full-Text | A Lightweight Perceptron-Based Intrusion Detection System for Fog Computing | HTML

Computational intelligence intrusion detection techniques in mobile cloud computing environments: Review, taxonomy, and open research issues - ScienceDirect

Intrusion Detection Honeypots: Detection through Deception: Sanders, Chris: 9781735188300: Books - Amazon
![Typical Network IDS Architecture [4] When a computer in a network... | Download Scientific Diagram Typical Network IDS Architecture [4] When a computer in a network... | Download Scientific Diagram](https://www.researchgate.net/publication/220014923/figure/fig1/AS:670048746237958@1536763478750/Typical-Network-IDS-Architecture-4-When-a-computer-in-a-network-communicates-another.png)