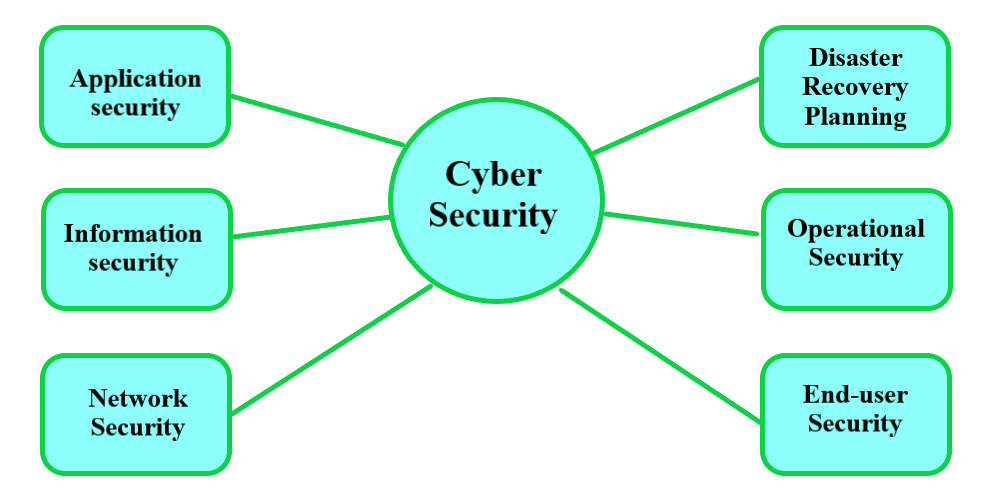
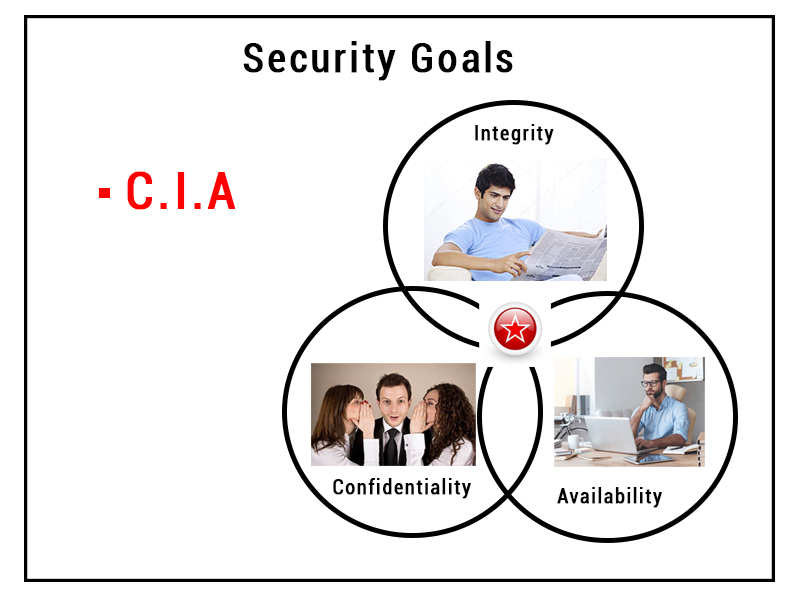
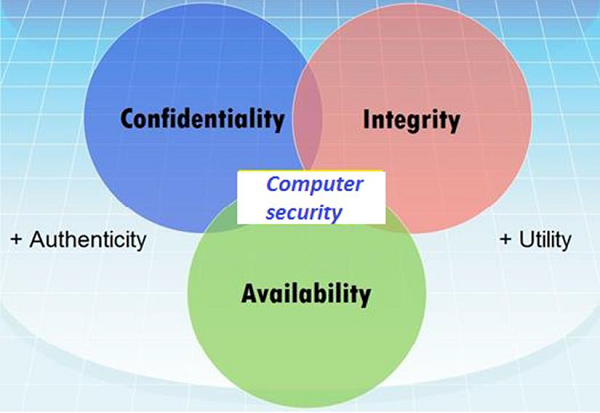
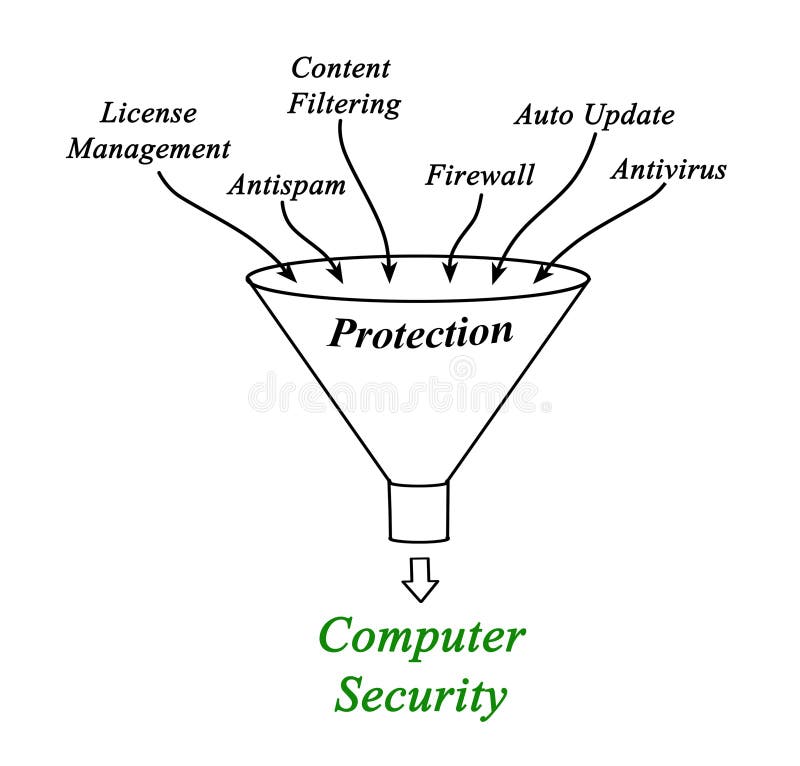
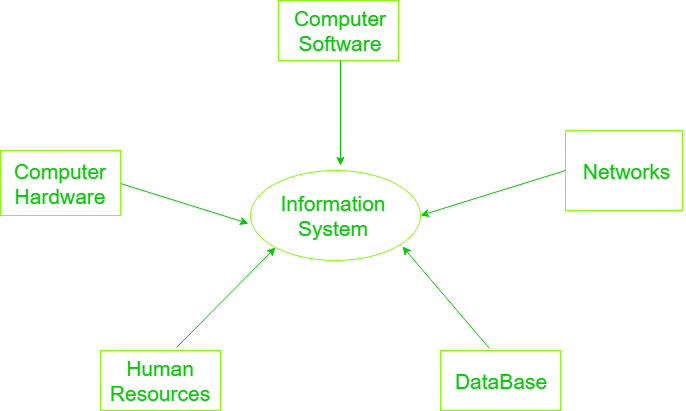
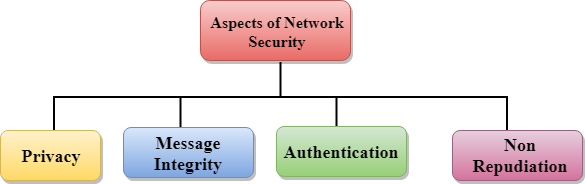
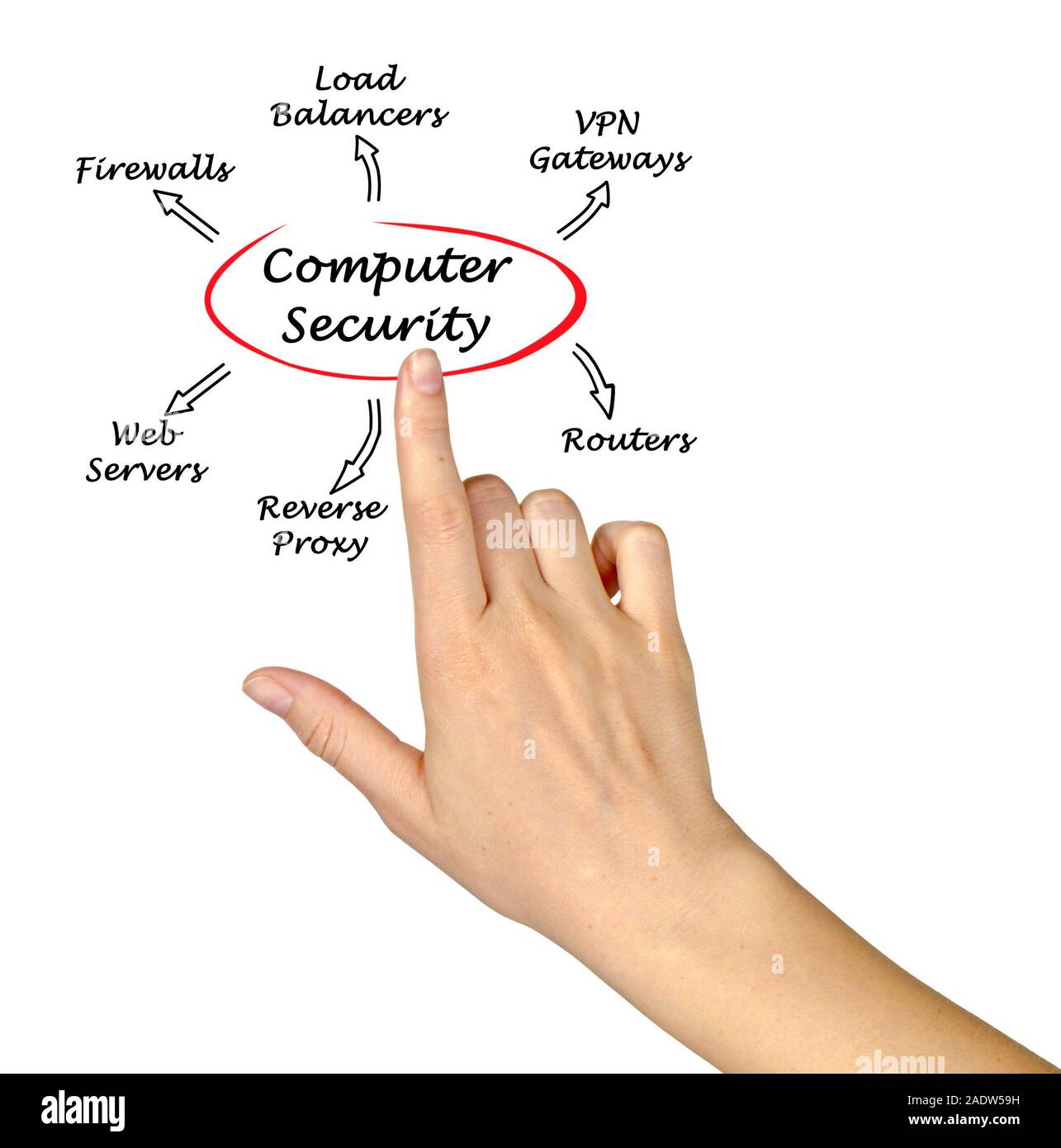
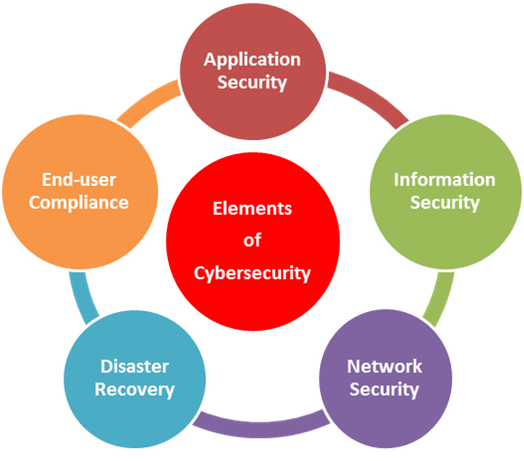
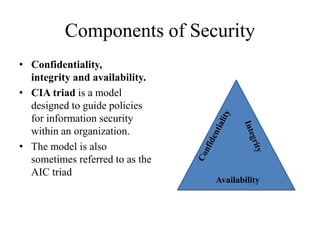
Chapter 1: Introduction Components of computer security Threats Policies and mechanisms The role of trust Assurance Operational Issues Human Issues Computer. - ppt download

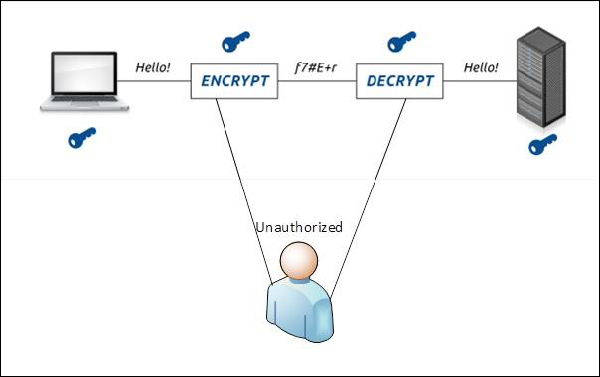
Cryptography and Computer Security: The life cycle of Passwords & Keys Life cycle and their relationship with your protection